Manage Windows Hello for Business with Intune
Windows Hello for Business can be deployed using a device configuration profile, which allows you to configure various settings on Windows 10.
With Intune device configuration profiles, you can permit or block the use of Windows Hello for Business, and you can configure the following settings:
- Minimum PIN Length
- Maximum PIN Length
- Lowercase Letters In PIN
- Uppercase Letters In PIN
- Special Characters In PIN
- PIN Expiration (Days)
- Remember PIN History
- Enable PIN Recovery
- Use A Trusted Platform Module
- Allow Biometric Authentication
- Use Enhanced Anti-Spoofing When Available
- Certificate For On-Premises Resources
You can also use Intune device enrollment policies to configure Windows Hello for Business settings during the initial device enrollment into management.
Configure PIN
To avoid sign in using passwords, Microsoft provides an authentication method that uses a PIN in association with Windows Hello. When you initially set up Windows Hello, you’re first asked to create a PIN. This PIN enables you to sign in using the PIN as an alternative—such as when you can’t use your preferred existing biometric method because of an injury, because the sensor is unavailable, or because the sensor is not working properly. The PIN provides the same level of protection as Windows Hello.
Windows Hello PIN provides secure authentication without sending a password to an authenticating authority, such as Azure AD or an AD DS domain controller. Windows Hello for Business provides enterprises compliance with the latest FIDO 2.0 (Fast Identity Online) framework for end-to-end multifactor authentication.
If the user does not use Windows Hello for Business, then the user cannot use an associated PIN. Within a domain environment, a user cannot use a PIN on its own. (This method of sign-in is known as a Convenience PIN.) You will see from the user interface displayed in Figure 1-20 that the PIN settings are within the Windows Hello section of the Sign-In Options. A user must first configure Windows Hello and be already signed in using a local account, a domain account, a Microsoft account, or an Azure AD account. The user is then able to set up PIN authentication, which is associated with the credential for the account.
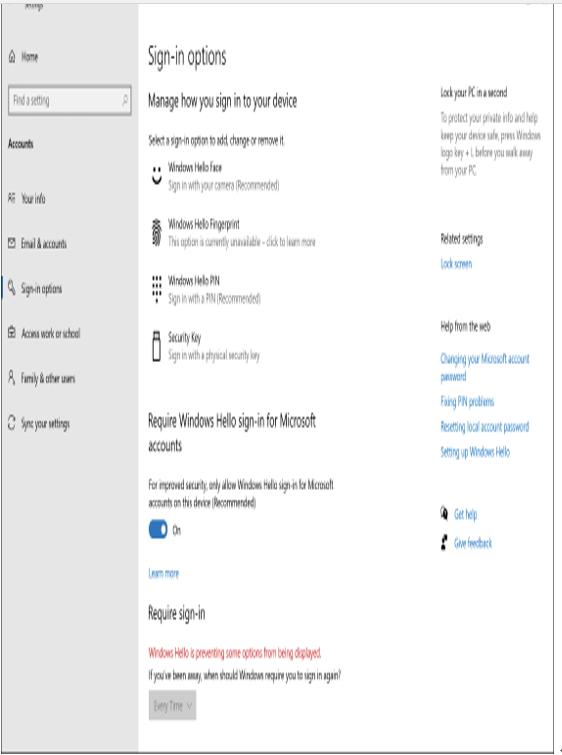
Figure 1-20 Configuring Windows sign-in options
After a user has completed the registration process, Windows Hello for Business performs the following operations to secure the credentials:
- Generates a new public-private key pair on the device known as a protector key.
- If installed in the device, the TPM is used to generate and store this protector key.
- If the device does not have a TPM, the Windows 10 operating system encrypts the protector key and stores it within the file system.
- Windows Hello for Business also generates an administrative key that is used to reset credentials if necessary.
Note Pairing of Credentials and Devices
Windows Hello for Business pairs a specific device and a user credential. Consequently, the PIN the user chooses is associated only with the signed-in account and that specific device. A user is unable to sign in on another device unless he or she initiates the Windows Hello setup on the device.
The user now has a PIN gesture defined on the device and an associated protector key for that PIN gesture. The user can now securely sign in to their device using the PIN; also, the user can add support for a biometric gesture as an alternative for the PIN. The gesture can be facial recognition, iris scanning, or fingerprint recognition, depending on available hardware in the device. When a user adds a biometric gesture, it follows the same basic sequence as mentioned earlier. The user authenticates to the system by using the PIN and then registers the new biometric. Windows generates a unique key pair and only stores this on the device. There is no Windows Hello biometric data stored in the Microsoft Cloud.
You can create and implement policies for using Windows Hello for Business in your organization. For example, you can configure a policy that enables or disables the use of biometrics on devices affected by the policy. If allowed to use Windows Hello for Business, a user can then sign in using the PIN or a biometric gesture.
Need More Review? Windows Hello for Business
To review further details about Windows Hello for Business, refer to the Microsoft website at https://docs.microsoft.com/windows/security/identity-protection/hello-for-business/hello-identity-verification.
You can use MDM policies or GPOs to configure settings for Windows Hello for Business.
Note Enhancing the Security of a Pin
When we think of a PIN, we generally think of ATM cash machines and four-digit PINs. When securing Windows 10 with Windows Hello for Business, you can significantly increase the level of security by imposing rules on PINs. For example, a PIN can require or block special characters, uppercase characters, lowercase characters, and digits. A PIN such as t496A? could be a complex Windows Hello PIN. The maximum length that can be set is 127 characters.
To configure PIN complexity with Windows 10 (with and without Windows Hello for Business), you can use the eight PIN Complexity Group Policy settings that allow you to control PIN creation and management.
These policy settings can be deployed to computers or to users. If you deploy Group Policy settings to both, then the user policy settings have precedence over computer policy settings, and GPO conflict resolution is based on the last applied policy. The policy settings included are as follows:
- Require Digits
- Require Lowercase Letters
- Maximum PIN Length
- Minimum PIN Length
- Expiration
- History
- Require Special Characters
- Require Uppercase Letters
In Windows 10, the PIN complexity Group Policy settings are located at Administrative Templates > System > PIN Complexity, under both the Computer and User Configuration nodes.