Azure AD Password Protection
Azure AD Password Protection offers a method to reduce the risk posed by your users choosing commonly used and compromised passwords for their access passwords. Using the password protection feature, administrators can populate a custom banned list of up to 1,000 passwords that users will be blocked from using. Also, you can choose to use the global banned password list.
Passwords that are deemed too common are stored in what is called the global banned password list. Cybercriminals also use similar strategies in their attacks. Therefore, Microsoft does not publish the contents of this list publicly. Administrators can use either a global banned password list or create a custom banned password list, which can contain lists of vulnerable passwords, such as the organization’s products, variants of their brand names, and company-specific terms. These can be blocked before they become a real threat.
The Azure AD Password Protection minimum licensing requirements are shown in Table 1-17.
TABLE 1-17 Azure AD Password Protection licensing
| Deployment scenario | Azure AD password protection with global banned password list | Azure AD password protection with custom banned password list |
| Cloud-only users | Azure AD Free | Azure AD Basic |
| User accounts are synchronized from on-premises Windows Server Active Directory to Azure AD. | Azure AD Premium P1 or P2 | Azure AD Premium P1 or P2 |
To configure Azure AD Password Protection for cloud-based accounts, perform the following procedure:
- Open the Azure Active Directory admin center (at https://aad.portal.azure.com) and sign in with a global administrator account.
- Navigate to the Security section and select Authentication methods.
- On the Authentication methods page, select Password protection.
- Under Custom banned passwords, select Yes for the Enforce custom list option.
- In the Custom banned password list displayed in Figure 1-15, enter a list of word strings. The words can have the following properties:
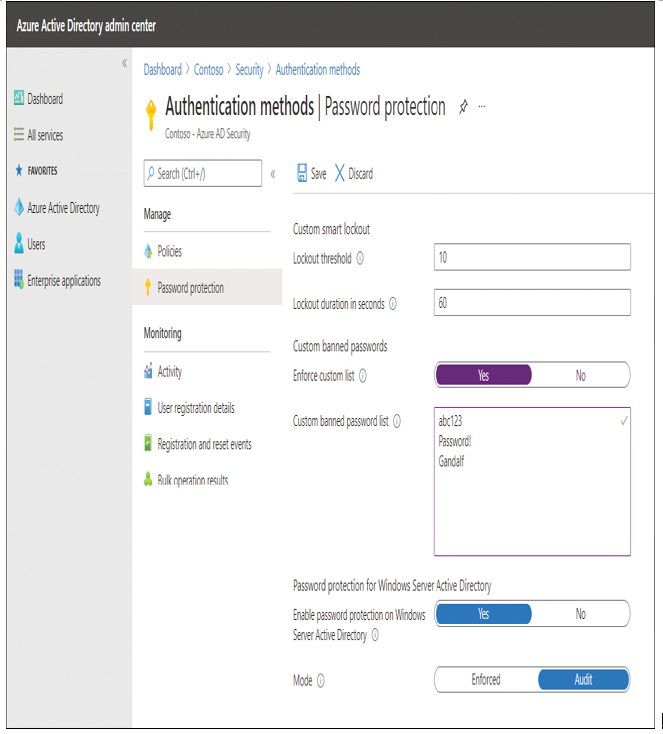
Figure 1-15 Azure AD Password protection
- Each word should be on a separate line.
- The list can contain up to 1,000 word strings.
- Words are case insensitive.
- Common character substitutions (such as “o” and “0” or “a” and “@”) are automatically considered.
- The minimum string length is four characters, and the maximum string length is 16 characters.
6. After you have added the word strings, select Save.
When users attempt to reset or update a password using a banned password, they see the following error message:
Click here to view code image
Choose A Password That’s More Difficult For People To Guess.
Azure AD Password Protection is also available for hybrid scenarios. To extend the banned password lists to your on-premises users, you need to install two components—one on your domain controllers and another on a member server, as follows:
- Azure AD Password Protection Proxy service Installed on a member server. Forwards password policy requests between your domain controllers and Azure AD.
- Azure AD Password Protection DC Agent & DLL Installed on your domain controllers. Receives user password validation requests, and processes them against the local domain password policy.
When users and administrators change, set, or reset passwords on-premises, they will be forced to comply with the same password policy as cloud-only users.
Note Azure AD Password Protection for Windows Server Active Directory
You can download the components required to configure Azure AD Password Protection for on-premises scenarios together with the full installation documentation at https://docs.microsoft.com/azure/active-directory/authentication/concept-password-ban-bad.